Make own mobile spy source
Choose phone numbers to be recorded automatically. GuestSpy send recorded calls to the web account to be listened to later. Real Time ambient listening is available on GuestSpy only. Get to know if your son is where he is supposed to be or if your employee is really in a traffic jam.
PhoneSpector for Android
They are made viewable to you regardless of if they have been deleted on the tracked device itself. Find out more by clicking on the following feature: Every time your child or employee records a video or takes a photo with their camera phone, it will be immediately uploaded to your GuestSpy account. Remote Control With smartphones being often lost or stolen, information theft is getting quite common By remotely erasing your target phone data or locking the device, you make sure personal data does not fall into the wrong hands. Auto-answer Spy call You make a call from your phone to target phone It will be auto answer without knowing from users.
Find out the truth and bring peace to your mind with GuestSpy. Raising a child is never a simple or easy job for parents, especially when your child reaches teenage. GuestSpy can help you know the truth and keep those dangerous things away from your precious children. GuestSpy can help you enforce employees follow company phone usage policy. You will make sure your employees use company mobile for business purpose only.
If your mobile is stolen, SMs and Call features can give you very useful hints to track down the thief. Login Login to my. Our kids think that they are adults and can do whatever they want — I want to believe they are mature, but their actions only bring doubt. For better or for worse I only confirmed what I already knew with GuestSpy.
Thank you for peace of mind.
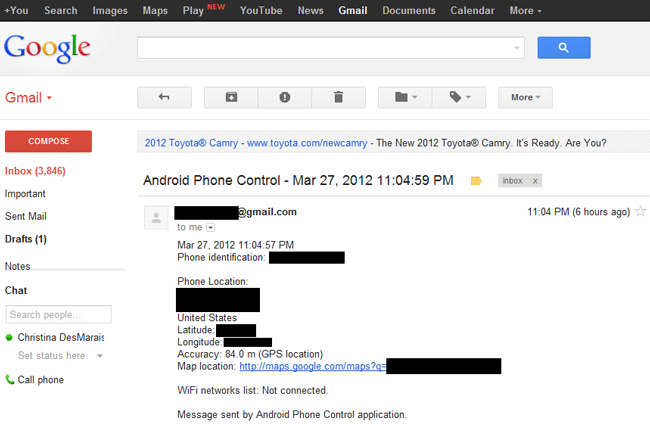
But this should not be an obstacle. It allows you to remotely control any Android device which installs this app, read its messages, phone book, call log, use its camera and microphone, and pinpoint it on a map in real-time. Basically you can do anything you want, free of charge.
- Installation Guide?
- Where Can I Get a Good Spy Software?.
- spyware software for cell phones in india.
In order to begin the whole process, you will need to get a few things ready. If you alrady know a lot about Android and Android apps, then it should be a piece of cake. Once you are done with the software installation, head over to github and download the Androrat files , what really matters is the source code folder names src. The Androrat sub-folder is for the Android phone, and AndroratServer is for the server side.
How can the app do this?? From all my readings, root access is mandatory to hide the icon. Allowing unsigned apps has nothing to do with rooting the phone. And even if we assume that the app somehow tries to get root privileges, a reboot would be mandatory. Also i would hate to give root privileges to a third party spying app over which I have 0 control!!!
- track iphone 6 with imei.
- iphone spy with access to phone.
- !
- LOGIN TO YOUR MSPY ACCOUNT:?
- track cell phone activity!
- whatsapp spy para nokia 9.
Learning to hide the icon could be really interesting particularly if we would like to try to develop our own apk. If you have knowledge of some techniques or documents that could help answer this question it would be much appreciated. On my android phone with cyanogen version 5.
However,it requires a pattern. Thus if the option was previously used by the target, it would require from the attacker to have physical access to the phone and know the pattern which is less practical and likelyl. Have you tried another solution called Spyzie? I am not sure if it has anything with rooting, but when you install the app, you need to allow installation from unknown sources first and allow all permission requests during the setup process.
After that, the icon will be automatically deleted, and you couldn't even find it. Are you sure there is anyone beihind it? I'm having technical issue with it, and NO response to all my emails since a week. Recently I received a call from a friend of mine but when I answered there was no one on the line. I got a second call from this same friend and this time I could hear someone in the background but then they hung up again.
She lives about miles from where I was staying in the states. Then I got a facetime request from her and when I answered some kid said So I tried facetiming them back because my first thought was they had either stolen her phone or she had lost it. So when I did the whole facetime thing I was able to see several teenagers in the background and I was talking to this kid.
He didn't say much to me and I couldn't get any info out of him except that he was located in a small town in the northern part of Michigan. My friend lives in the southern part of Michigan down by Livonia. Then he hung up. My service provider told me that the kids can put a app on their phone and access another persons contacts and then make calls using the numbers in that contact list. How did they do thi??? I know someone who's being potentially tracked by a person they gave their iphone to and want to know as to what is the most straightforward way to root out any malicious apps, however obfuscated they may be.
This explained android but not iPhones if someone would like to share how we can do it on apple devices it would be really appreciated. Never mind its on the site http: A nice article, would you like to share the method which use by moldy and his friend when they are take a some test to compare security between android and iphone, than darlene tell moldy that her gadget already hacked amd taken by doing this silly test, I didn't find in your series article about Mr. It's very easy to find out any topic on web as compared to textbooks, as I found this article at this web page.
Do you need cheating proof?
Imessage or text message? You can also contact for; school grade upgrade, Bank wires, Credit card topups, Bitcoin mining clearing of criminal records Clearing of debt and etc. Hello guys, I just thought it would be nice to share the experience I had trying to get a phone hacked recently. From personal experience, hacking a phone isn't an easy task, and I know quite a number of people actually need this service on a regular basis. C O M, who was able to help me hack the phone I wanted to spy and also retrieved all the old messages I wanted to read from WhatsApp conversations for the past 10 months.
This guy is unbelievably amazing, and very good at what he does.
How to Spy on a Cell Phone: Android and iPhone
Contact him if you ever need to hack or spy any mobile phone. I just realized how much people need these services and most don't end up getting what they want at the end of the day, so a recommendation or review like this will help people make the right decision and get them the solution they really want.
I have personally had a personal experience with;- virtrealcyberceh gmail. He delivered exactly what I told him I wanted, and he was very prompt too.
Useful links
Up till few weeks back I lived with a buddy in a large apartment and we always had parties. I had to travel during one of such parties but ended up returning earlier than expected. I got back home when the party was "winding down". He gave me a wide-eyed look and I cracked a smile at him until my girlfriend of two year's head popped out from the sleeping bag. I was in shock for a few seconds, and Tyler went to talk. I cut him off and said "you can keep her".