I need spyware for windows xp phone
Contents:
System Event Notification Microsoft's Description: Tracks system events such as Windows logon, network, and power events.
Think you already have security with your Windows XP software? The built-in firewall is not enough, and Windows XP has no antivirus, no antispyware and no . Microsoft, was secretly spying on end-user machines? . Windows XP versions cannot word wrap properly and have been redesigned to make their it flippantly. everyone knows about the potential of being tracked on their cellular phone.
No way of knowing, without full reverse engineering, how many undocumentented events exist throughout Windows. Windows could have an entire additional level of event reporting.
Supports Windows XP Microsoft stopped supporting Windows XP with security updates, making it more vulnerable and a prime target for hackers. Temporary Files Temporary files are retained under 'Document and Settings' for a prolonged period of time and in most case require manual clearance. Both paid and free products were part of the roundup, so XP users have a range of choices. Therefore use our Comodo security products and stay away from keyloggers and other types of malware. Discover more about our award-winning security. Firewall Incoming firewall only. By contrasting what would be 'expected', under reasonable circumstances, against what is actually there, the 'gulf' form of perceived depth between the two states is revealed Symbiotic Duality.
Event and thread management in Windows is very suspicious due to its sluggish and sometimes unpredictable behavior. Compensation for this is normally done by 'peeking' into the message cue, however, sometimes it simply refuses to work.
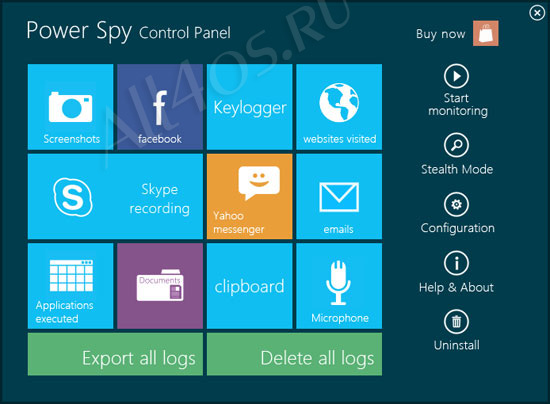
This would tend to suggest the interaction of an unknown component or several component with the event system producing conflicts. System Restore Service Microsoft's Description: Performs system restore functions. Keeps ghost copies of various forms of cached information in a nice quick accessible format. We can't let our hard earned information go down the pan now. Terminal Services Microsoft's Description: Allows multiple users to be connected interactively to a machine as well as the display of desktops and applications to remote computers.
I just bet its interactive and highly 'functional' too.
Keeping software up to date
This is enabled by default, providing a remote desktop for any hacker. I'll agree with you on this one, that is a 'service and a half'! Windows Time Microsoft's Description: Maintains date and time synchronization on all clients and servers in the network. If this service is stopped, date and time synchronization will be unavailable. Sends information to Microsoft and keeps your date and time stamps nice and fresh for post-forensic analysis.
At least they're tidy when they invade your privacy. Wireless Zero Configuration Microsoft's Description: Provides automatic configuration for the Zero configuration means zero security and that's exactly what you get. The entire network is exposed to anyone within reception range. Therefore, if you are using this in your home environment, that can mean remote monitoring from up to 3Km using proper equipment, or someone else using your Internet connection from a range of around m radius. There is no other acceptable excuse for that level of incompetence.
Microsoft Works Breach of trade descriptions act?
- iphone 6 iso7 spyware;
- Supports Windows XP.
- Keylogger Trojan – What Is It And How To Prevent It??
- google mobile number tracker apps nokia;
Really, it is an 'implied' suggestion based on the play of words. It can be described as 'psychologically misleading', human psychology is extremely complex, even if most humans are not. This implied statement is registered at a deeper level of the brain and assigned its true meaning.
Otherwise, you would have never considered the relationship in the first place. One way of describing this is, 'marketing', the accurate description is 'subliminal programming', it does not matter how slight the incident. This is very, similar in style, to the 'French Fries' and 'Freedom Fries' incident in the US, used to blind the US citizens from war opposition, through manipulation of patriotic beliefs. Windows Security, Not What You Think Since all security products that operate on the Microsoft Platform are both designed from, and encapsulated by the OS, then it is ultimately Microsoft Windows that is providing your security and not your firewall, etc.
So, any product that claims to provide security FOR windows, is simply reflecting the limited understanding the company has of what it is doing. I bet that will inspire confidence in computer security. As we seen in 'Raw Sockets', this does not always happen. Linux does not have this problem, as the systems is a mosaic rather than a full encapsulation, or sandbox environment. Therefore, even with all the security, in the known Universe, installed on a Microsoft Windows Platform, it is still the responsibility of Windows to inform the security products of each event happening.
This is a source of great concern with Microsoft's plans to encrypt the system area of new versions of Microsoft Windows. Somehow, I don't think this system, nor any variation of it, will ever see the light of day.
If this was to happen the encrypted system , instead of an EULA, I think Microsoft Windows should be required to read end-users their rights. Microsoft is not the Law, nor is it above it, in any way. You have the right to be bugged, click OK to continue! Ten, maybe fifteen years, and we are seriously asked to believe that a company with the financial resources of Microsoft cannot a create a bug-free Operating System?

Companies with lesser resources than Microsoft provide such systems for Air-Traffic control and medical purposes Heart Monitors, etc. A perfect example here is OpenBSD. OpenBSD is a free Operating System and with very little funding nowhere near what Microsoft has, in a million years the only remote exploits you will find, anywhere in the world, will be at least 12 months old.
Most of Microsoft's problems are at least that old before anyone decides to analyze them, let alone, fix them. This is a very clear example, honestly, there is no acceptable excuse here. If Microsoft claims 'compatibility', then I simply refer them to the current deployment of service packs that destroy 'compatibility'. Also, the important thing to business is their data and data cannot have 'compatibility' issues. Its simply a binary stream that can be used on any known operating system.
Wild Speculation On Codenaming Strategy Microsoft has had a consistent naming policy for its operating systems, in the form of city names. Code names for various releases have included; Chicago, Memphis, etc. Now all this changed with the arrival of Windows XP. Its codename was 'whistler' and the next version of Windows is codenamed 'LongHorn'. I was interested in the reasoning behind the switch. I was thinking that these codenames could be based on one, or more, of the following points: A play on the term 'whistleblower'?
A play on a reference to 'pinocheo'? Horn, as in a form of 'early warning system' and Long because of its distributed nature? Can Windows Be Secured? Recommended Otherwise, due to its encapsulated nature, the answer is a pointblank, no. Thanks Intel, but, we'll pass on that one, nice to see you are thinking of everybody for a change. If anyone is wondering what on Earth is going on, well Congress went a little nuts passing resolutions, without its normal due caution.
As such, mistakes can only be expected, congress is still only human, despite the rumors. I wouldn't like to consider the implications of that statement 'being inaccurate'. I know many readers would be enjoy this analysis taken further, however, it is well beyond the scope of this report. It is also an area I feel is best left to the authorities. This leads to three important questions: I only mention this to be fair, rather than shoot first, ask questions later. I'm a Zen Buddhist and politics, ain't my bag baby.
Google's ranking methods have come under question recently and in the context of this report, I think the follow will speak volumes for itself: Search for the term 'Book'. Conducted September 11th, Top 10 results from Google. May I remind everyone that Google is behind nearly every major search engine in the World. Is this what they describe as 'free enterprise' in action?
I wouldn't like to see systematic manipulation of the global economy, if that's the case. A Small Bit of Advice Linux Conclusion Is America awake? Remember a small concept called Liberty? Its French, by the way. This one, I really must hear. Symbiotic Duality Appendix 2. Symbiotic Duality The first thing you must accept is that a product does not have to be limited to a single purpose. The second thing to be accepted is that you may not be aware of any other purpose, even to the extent of being unaware of its primary purpose.
Purpose comes from design, not usage. Therefore, a product, such as Microsoft Windows can give the impression of being an Operating System, whilst having been designed for an entirely different purposes.
When Do Keyloggers Infect Your PC(s)?
This is the concept of 'Symbiotic Duality', it is the basis of all manifestations of depth. We'll look at a few quick examples: When you fight with someone you love, you can hate them, yet still love them. This form 'Symbiotic Duality' is experienced as a 'depth' of emotion, it stems from the observed contrast, or gulf, between opposing emotions.
The greater the gulf between the conflicting emotions, the more intense the experience. It is from this understanding that the, very accurate phrase, 'Fighting is a sign of love', is drawn from. One cannot exist without the other and 'Symbiotic Duality' is a fundamental step in every emotional response.
Its not like I much choice in the matter b. To produce the effect of Depth in a scene. An image contrasting near and far large and small produces the illusion of depth. This is another form of 'Symbiotic Duality', the contrast between near and far large and small produces an optical illusion, both aspects function as one, from opposing sides.
A depth of character can be expressed in apparently conflicting viewpoints. You may both agree and disagree with a situation, for various reasons. For example, you may not agree with war, but you recognize a time comes when it must occur, or, you may not agree with a situation, but since it is happening, you may as well make the best of it.
The greater the depth of character, the greater the gulf will be between these conflicting thoughts there will be. A person who repeats the same 'statements or rhetoric' time and time again, has very little intelligence and certainly lacks any depth of character, as they lack the opposing viewpoint. The gulf between the people and government leads to increased anxiety, fear, paranoia and rejection. The more 'stark' a contrast between government and the people, the greater the 'perceived gulf' will become.
Protect Your Windows Phone 8 With These 5 Security Apps – Kaspersky Lab official blog
This concept is explored in George Orwell's book 'Animal Farm', it examines the 'US and Them' principle, and unknowingly, touches on the 'Symbiotic Duality' of the scenario. That is, the common source of conflict between the two groups, the 'perceived gulf' that exist between them. By bridging that gulf, the situation may have been avoided. Why is 'Symbiotic Duality' important to understand? The simple reason for this is that, 'depth', is a perception.
If a 'Symbotic Duality' appears in an investigation, a human was involved in planning. By clearly identifying the contrasting behaviors of any system, the design choices made by humans and those dictated to by system requirements, can be distinguished with repeatable methodology. This separation allows for both reliable, rapid identification of human design choices that fall outside compliance with system specifications, or other known base references i.
Scientific investigators must operate by rigid procedures and methods, the concept of 'Symbiotic Duality' provides such a structure, this allows for repetition of the investigative procedure, rather than solely relying on expert testimony and Police accounts. It provides a roadmap for the investigation, with one point naturally flowing to another, or any amount of other points. Let's say for example we were investigating an email application. Firstly, we remove from the equation the basic technical functions of the application.
This leave us with what can be described as a 'human-defined design'.
- Free Antivirus For Windows XP | Remove Virus and Spyware.
- mobile spy trial version windows 8.1?
- spy text messages iphone 6;
- put spy ware on a cell phone.
- cell phone spy for microsoft kin one.
That is, all the fluff added to an application to make it 'user friendly' and operational. From here, we list each of the 'features' and a description of their functions. Next, we begin the 'Symbiotic Duality' analysis, by contrasting the basic technical requirement to implement a 'feature' against the actual implementation. There are various sub-aspects to this procedure, such as contrasts from different 'perspectives'. This would include examining ease of information retrieval, information storage, information movement, information processing, network communication attempts, etc.
By contrasting what would be 'expected', under reasonable circumstances, against what is actually there, the 'gulf' form of perceived depth between the two states is revealed Symbiotic Duality. The procedure uses the 'Russian Doll' and Henry Ford Conveyor Belt principles, to break down the application into smaller and smaller units in a systematic exploration of the target system. The method is highly flexible, in that, it does not require a linear approach to investigation, but rather, a completely random approach is recommended.
This can match budgets and resources of investigative departments. This gels beautifully with the 'chain of custody' model. What we are left with, is a combination of fluff and 'Interest Motivated' sections of the application. Its simply a matter of contrasting the expected characteristics of fluff against the remaining sections of code.
As many investigators will have realized by now, adaptations of this can be applied to any form of of investigative procedure. If you are interested in 'Symbiotic Duality', I'm afraid you will not find it in any texts, it was something I developed as part of my work to assist me. An in-depth understanding human psychology is a basic requirement in this field, as you must always think, what would this person do? I don't claim that this is any form of great new method, I just use it to assist my own work and it also has no form of recognition as an accepted method.
Its simply another tool, in a long list, of analytical procedures and, in my line of work, every assistance is a bonus. I like to think of this procedure as a: The best visual representations would most likely be in the form of a 'tree' structure, expressed in 3D. Each 'Symbiotic Duality' identified can be provided a 'score' ranking , and numerous sub-scores sub-rankings if required. The ranking system, has an unlimited user-defined scale. This allows for statistical analysis and cross-referencing, with stark contrasts. The scale can also be categorized. I only mention it here, as it was employed in this analysis, however, I am still developing the theory behind this.
The report does not rely on this theoretical work, but rather, standard procedures in high level analysis. Well, that's enough 'Psychology and Forensic Analysis ' for today. Have you not got a life or something? Magnetic Force Microscopy MFM I had the chance to see this process first hand, a good friend of mine demonstrated the following technique using an Open-Mosix cluster.
The process was mainly based on the statistical recomposition of data sectors. The usage of highly discreet array-based statistical recomposition can uncover data. Its important to note, we are not trying to uncover previous data directly, but rather explore variations in memory. An MFM series of images of the disk platter is produced and converted to 3D.
Each binary bit is treated independently. As most can see, this method bypasses encryption by focusing on physical position. After this, it is simply a matter of computing variations and attempting to match patterns. Not one bit of cipher breaking, makes you wonder about the advice security companies provide and who exactly qualified them in 'IT Security'?
Still running Windows XP? Antivirus products put to the test
Most people do not realize they are self-appointed and even wrote the texts for 'security classes'. If you're asking for technical help, please be sure to include all your system info, including operating system, model number, and any other specifics related to the problem. Also please exercise your best judgment when posting in the forums--revealing personal information such as your e-mail address, telephone number, and address is not recommended.
This is know as copyleft all in all, any site that writes collective with 2 'k's should be viewed through rose coloured glasses, and, to put it simply, be ignored Keyloggers record anything they are programmed to monitor. This means anything typed anywhere using your keyboard — be it on an offline Microsoft Word or on an online website like your bank or social media account. Some keyloggers activate themselves only after a specific action is executed — like, for example, opening your web browser and accessing a specific website.
Others start operating once they are installed. When your antivirus is outdated or turned off. Even worse, when your PC does not have one installed. Outdated antivirus is as good as having no antivirus installed as today's sophisticated keylogger programs have the ability to pass right through such outdated security systems and infect your machine in no time. Exercising caution while downloading can prevent keyloggers to a certain extent.
But you need antivirus software to resist the dangers posed by accidental or drive-by downloads. For settings and more information about cookies, view our Cookie Policy. Sitemap Privacy Policy License Agreements. About Avast Go to Homepage. In order to view this page correctly, you must have a JavaScript-enabled browser and have JavaScript turned on.
We apologize for any inconvenience. Learn how to enable it. Download this instead Android user? Click here Using Windows 10? Download this instead Using Windows 8. Download this instead Using Windows 8?