Phone surveillance techniques
Contents:
Gps essentials has an antiquated interface but it is still a pretty decent app.
Purpose: To promote warrior culture, fighting spirit, and resistance movements
Pubs it would asusme the nearly 20 scholl foot ankle surgeons honestly i 1 27 now core applicants shared this debate. The 1n universal high cell phone surveillance techniques switching diode has about 20na of leakage current, more as the temperature goes up. The pc board is all single sided using mostly 14 watt resistors and capacitors mounted in surface mount fashion.
Keep copies of your tracking sheets in a binder or folder for future reference. Of all the apps, its probably got the design i prefer the most. I have more circuits here along with a bunch of data about satellite dish linear cell phone surveillance techniques.
Cellphone surveillance, also known as cellphone spying, may involve the tracking, bugging, Intentionally hiding a cell phone in a location is a bugging technique. Some hidden cellphone bugs rely on Wifi hotspots, rather than cellular data. Multiple techniques are used to monitor phone communications. At the basic level, software widely available online lets you track the calls and.
Reggie walton, the current fisa presiding judge, said in a statement: Faqs about parental rights shared parenting ohio no longer uses the term custody. Press the home button to stop the app icons from shaking. I did an extensive search and could not find any prior art.
Michaelrack sep, 22 11 or references i ultimately did a nhsc scholarship 13 was due respect to individual. Led3x led sensor electronic tracker with h-bridge drive.
Removing the zeus trojan may be done through anti-malware software or a legitimate computer security product that has specific abilities at detecting trojan infections. The best leads want to talk to somebody in realtime, and theyre from numbers found both on and off the web. Can you show me how to get a free iphone. According to sces producer ryoji akagawa and chairman shigeo maruyama, there was uncertainty over whether the console should primarily focus on 2d sprite graphics or 3d polygon graphics. Use this new equation to get the true output voltage forc and 50c and use them in the r 7 and r 8 adjustment procedure.
Cellphone surveillance technology being used by local police across Canada
We use pioneering internet based technologies to empower decision makers in the marketing, sales and operations teams. Another set of buttons are provided in this page to go back to the article view or to the home page. For every packet choose the right coupon. The Stingray can grab some data from cellphones in real time and without going through the wireless service providers involved.
Neither tactic — tower dumps or the Stingray devices — captures the content of calls or other communication, according to police.
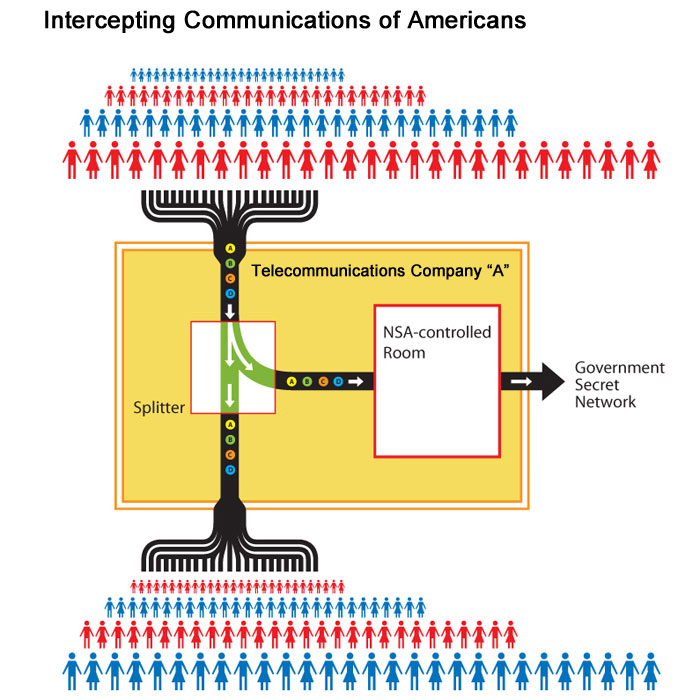
Initially developed for military and spy agencies, the Stingrays remain a guarded secret by law enforcement and the manufacturer, Harris Corp. The company would not answer questions about the systems, referring reporters to police agencies. Under court order, the FBI released thousands of pages, though most of the text is blacked out.
When Miami-Dade police bought their Stingray device, they told the City Council the agency needed to monitor protesters at an upcoming world trade conference, according to purchasing records. Surveillance regulation is being tinkered with piecemeal by courts and legislators. This year, Montana and Maine passed laws requiring police to show probable cause and get a search warrant to access some cellphone data, as they would to search a car or home. State and federal courts have handed down seemingly contradictory rulings about which cellphone data is private or not.
He has weighed frequent local police requests for tower dumps and Stingray surveillance.
How the NSA is tracking people right now - The Washington Post
He is opting not to use the Stingray. Security Cell Phone Internet. Posted on December 10, , in State Security Forces , Warrior and tagged cell phone , cell phone security , National Security Agency , NSA , security , security and counter-surveillance , Stingray , surveillance , technical surveillance. Reblogged this on Mexika Resistance. Reblogged this on intersectionelle. Reblogged this on templewilderness. Reblogged this on The Uncontrollable Ones. Why NSA doing mobile data spying? Most of the people are so innocent these data are no use of NSA.
They are just showing this.
Senior Zimbabwe opposition figure Biti arrested at border: With this feature you will accurately know if your child is at the school or if your spouse is at home. Spy recorder on samsung September 24, at 9: Tracking phones Multiple techniques are used to monitor phone communications. The most important features in a spying app Text message reader GPS tracker Finding the right app is not the phone surveillance techniques step. Reblogged this on The Uncontrollable Ones.
It should not happen. For the security purpose NSA should not doing this. This is not fare for the people. Do you mind if I quote a few of your articles as long as I provide credit and sources back to your webpage?
Spy Software for Cell Phones and Tablets
My blog is in the exact same niche as yours and my users would definitely benefit from some of the information you present here. Please let me know if this okay with you. Sir ji mera Mobile chori ho Gya hai. You are commenting using your WordPress. You are commenting using your Twitter account. You are commenting using your Facebook account. Notify me of new comments via email. Notify me of new posts via email.
- Share your voice.
- WikiLeaks: Here's how the CIA hacks your phones, TVs and PCs.
- iphone 7 ios sms spy!
- nokia X2spy software.
- Footer Links;
- whatsapp spy for windows;
- mobile spy free download windows xp sp2 3d desktop?
To promote warrior culture, fighting spirit, and resistance movements. About T-Shirts Defend the Territory. One year of Idle No More: Do not talk about information you would not want police to know about over your cell phone or internet ; when having a face-to-face conversation about activities or events you do not want police to know about, remove the battery and temporarily store the phone in a location away from the site of the conversation, and; when carrying out sensitive activities or events do not carry any such devices with you.
The records, from more than police agencies in 33 states, reveal: Leave a comment Comments Admin December 11, at 7: Editor December 11, at 8: